In the world of cryptography, Caesar Cipher is considered to be one of the simplest yet historically important encryption methods in simple words Caesar cipher is one of the foundations in the world of cryptography despite being the simplest and easiest to crack in today’s era. It is named after Julius Caesar who used this technique to communicate during wars. Caesar Cipher technique works by just shifting each letter of a text by a particular number in the alphabet. Despite being very basic in cryptography, it provides valuable insights into the fundamentals of encryption-decryption and serves as a foundational concept in the study of cryptographic techniques.
To read more such blogs, click here.
How exactly the Caesar Cipher works
The Caesar cipher works on the basic principle of substitution where each letter of a text is replaced by a letter occurring at a fixed number of positions in the alphabet. This fixed number is referred to as a “shift” or “key” and determines the degree of encryption applied to the message.
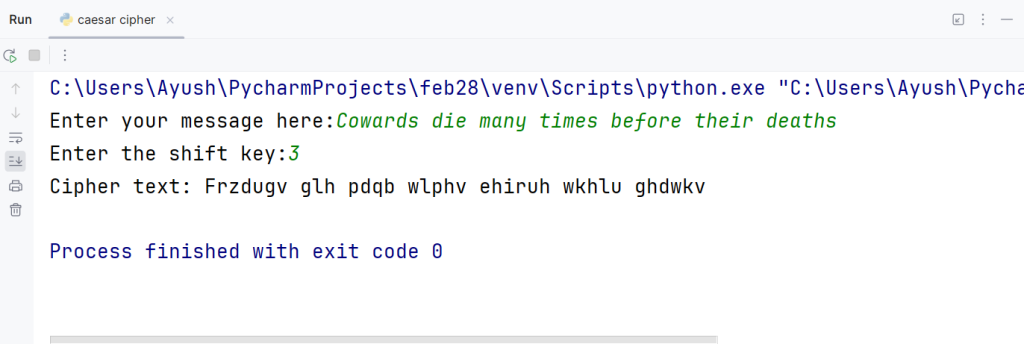
For Example: If the shift is 3, A will be replaced by D, B will be replaced by E, C will be replaced by F, and so forth.
Now let us create a program in Python language with the help of which we can create an encrypted text for any message.

You are reading Exploring the Caesar Cipher: A Classic Encryption Technique
Step 1: Let us create a function called caesar cipher()
def caesar_cipher(text, shift): # defining a caesar cipher function
encrypted_text = ""
for char in text:
if char.isalpha():
ascii_val = ord(char) # Get the ASCII value of the character
if char.isupper(): # Check if the character is uppercase or lowercase
# Shift the character's ASCII value and handle wrap-around
shifted_ascii = ((ascii_val - 65 + shift) % 26) + 65
else:
shifted_ascii = ((ascii_val - 97 + shift) % 26) + 97
# Convert ASCII value back to character and add to the result
encrypted_text += chr(shifted_ascii)
else:
# If the character is not an alphabet letter, keep it unchanged
encrypted_text += char
return encrypted_text- This function is created with parameters text(message from the user) and shift(positional number of substitution).
- After that, we created a variable named encrypted_text as an empty string.
- Now we will use a for loop in the variable text which will access every letter in the text variable by the variable char.
- After that, we will check whether the character is an alphabet or not then we will create a variable ascii_value which will hold the ASCII value of that character.
- Now we will check if the character is in upper case., we will create a variable shifted_ascii which will store a new ASCII code on behalf of the shift value.
- Numbers like 65 and 97 are used so that the upper letter gets substituted by the upper letter and the lower with the lower alphabet. Similarly, modulus by 26 is used because there are 26 alphabets in English.
- If the character is not in upper case, the interpreter will jump to the else part and generate the new shifted_ascii value for the lower case character.
- The variable encrypted_text will be updated by the character itself converted from ASCII code to an alphabet.
- If the character is not an alphabet, it will be updated in the encrypted_text as it is.
- In the last step of the function, we will return the encrypted_text.
You are reading Exploring the Caesar Cipher: A Classic Encryption Technique
Step 2: In this step, we will receive a message from the user and the shift amount.
plaintext = input('Enter your message here:")
shift_amount = int(input('Enter the shift key:')
cipher_text = caesar_cipher(plaintext, shift_amount)
print("Cipher text:", cipher_text)We will receive a message from the user and store it in a variable named plaintext and then the shift amount. After that, we will call the function caesar cipher with arguments plaintext and shift_amount and then save the returned output into the variable cipher_text.
At last, we will print the cipher text.
You are reading Exploring the Caesar Cipher: A Classic Encryption Technique
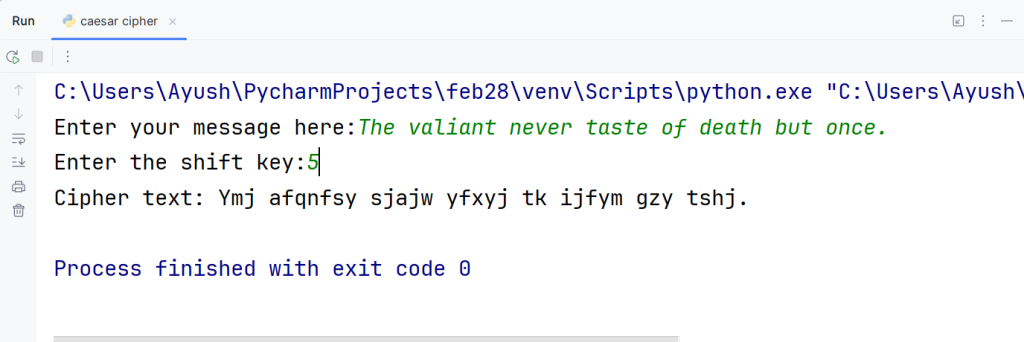
Step 3: It is time for the output now.
For more such content and regular updates, follow us on Facebook, Instagram, LinkedIn
Python is the easiest and a general-purpose programming language which means it can be used to perform a variety of tasks whether web-based development, software development, data analysis, and a lot more. This program is just an example of the easiness of Python programming language.
Right now, data science has become one of the fields where companies are hiring regularly and there is a lot of gap in the demand and supply of data analysts in the market.
If you wish to learn more about data science or want to curve your career in the data science field feel free to join our free workshop on Masters in Data Science with PowerBI, where you will get to know how exactly the data science field works and why companies are ready to pay handsome salaries in this field.
In this workshop, you will get to know each tool and technology from scratch that will make you skillfully eligible for any data science profile.
To join this workshop, register yourself on consoleflare and we will call you back.
Thinking, Why Console Flare?
- Recently, ConsoleFlare has been recognized as one of the Top 10 Most Promising Data Science Training Institutes of 2023.
- Console Flare offers the opportunity to learn Data Science in Hindi, just like how you speak daily.
- Console Flare believes in the idea of “What to learn and what not to learn” and this can be seen in their curriculum structure. They have designed their program based on what you need to learn for data science and nothing else.
- Want more reasons,