encryption and decryption
In this blog, we are going to create a program that will create an encrypted message for any text inputted by the user but before that let us have a brief history of encryption and decryption
In the world of cryptography, Caesar’s cipher is considered the base of the advanced encryption and decryption technique that was used by Julius Caesar. In today’s time, encryption and decryption are the two important aspects where encryption works when a message is sent so that the message can be converted into such a code that it does not get compromised then comes the decryption part which is used at the receiver’s end. Decryption helps the receiver to convert the code into a normal and readable message. The decryption involves the key pattern on behalf of which the message has been converted into a code
To read more about Caesar cipher, click here.
The same concept is used even today by the name of encryption and decryption where the message is encrypted from the sender’s side first and then it gets decrypted from the receiver’s end to read the actual message and the decryption is done with the help of key which holds the information of encryption-decryption pattern.
Now we are proceeding with the program which can encrypt the message provided by the user and then decrypt it in a step-by-step manner.
You are reading Empowered Encryption and Decryption in 5 steps
Step 1: In this step, we will import the string module and random module.
import string
import randomThe purpose of importing the string module is to use some of the string functions that can help us to create a variable that has the collection of all the characters we may need(digits, lower alphabets, upper alphabets, punctuations, etc).
The purpose of importing the random module is to generate random patterns on behalf of which we are going to encrypt a message.
For more such content and regular updates, follow us on Facebook, Instagram, LinkedIn
Step 2: In this step, we will create variable chars and key.
chars=' ' + string.digits + string.punctuation + string.ascii_letters
chars=list(chars)
key=chars.copy()
random.shuffle(key) We will create a copy of chars and store it in a variable named key and then shuffle the items of this list variable key using random.shuffle(). This variable will be responsible for creating different patterns. In case of encryption and decryption key plays an important role to code and decode the message.
You are reading Empowered Encryption and Decryption in 5 steps
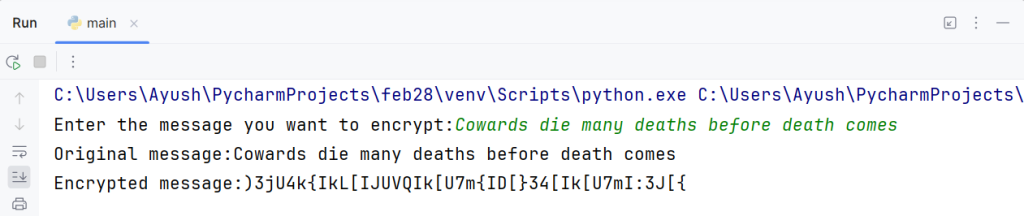
Step 3: In this step, we will receive a text from the user and then encrypt it.
# Encryption
normal_text=input('Enter the message you want to encrypt:')
cipher_text=''
for letter in normal_text:
index=chars.index(letter)
cipher_text=cipher_text + key[index]
print(f'Original message:{normal_text}')
print(f'Encrypted message:{cipher_text}')normal_text is a variable that we have used to receive a message from a user and then an empty variable called cipher_text. After that, we will use for loop to access all the characters from the normal text one by one with the help of variable letter.
Now we have to check the position of the current letter in the chars variable and store that index number in the index variable and then we will update the variable cipher_text by adding a character from the list variable key using the same variable index.
Now we can print original messages as well as encrypted messages.
You were reading Empowered Encryption and Decryption in 5 steps
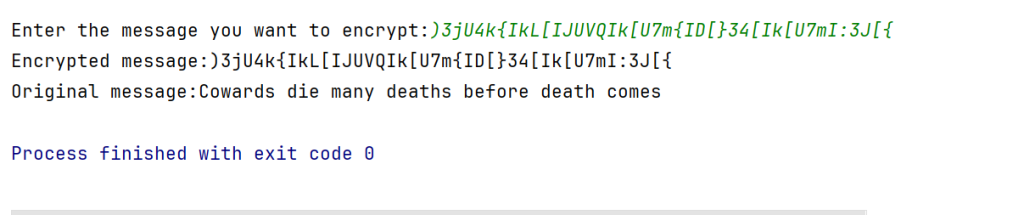
Step 4: Now we are going to create a logic for decrypting the message.
# Decryption
cipher_text=input('Enter the message you want to encrypt:')
normal_text=''
for letter in cipher_text:
index=key.index(letter)
normal_text=normal_text + chars[index]
print(f'Encrypted message:{cipher_text}')
print(f'Original message:{normal_text}')cipher_text is a variable where we will receive a decrypted message from the user while normal_text is another variable which is an empty string.
Now we will start the for-loop and access the letters stored in cipher text. After that, we will find out the index number of that letter in the key list and then concatenate the normal_text variable with the letter that is present in the chars list at the same index number.
Now we will print the encrypted message as well as the original message.
You are reading Empowered Encryption and Decryption in 5 steps
Step 5: The Output
Now we need to decrypt this message.
You are reading Empowered Encryption and Decryption in 5 steps
Python is the easiest and most general-purpose programming language which means it can be used to perform a variety of tasks whether web-based development, software development, data analysis, and a lot more. This program is just an example of the easiness of Python programming language.
Right now, data science has become one of the fields where companies are hiring regularly and there is a lot of gap in the demand and supply of data analysts in the market.
If you wish to learn more about data science or want to curve your career in the data science field feel free to join our free workshop on Masters in Data Science with PowerBI, where you will get to know how exactly the data science field works and why companies are ready to pay handsome salaries in this field.
In this workshop, you will get to know each tool and technology from scratch that will make you skillfully eligible for any data science profile.
To join this workshop, register yourself on consoleflare and we will call you back.
Thinking, Why Console Flare?
- Recently, ConsoleFlare has been recognized as one of the Top 10 Most Promising Data Science Training Institutes of 2023.
- Console Flare offers the opportunity to learn Data Science in Hindi, just like how you speak daily.
- Console Flare believes in the idea of “What to learn and what not to learn” and this can be seen in their curriculum structure. They have designed their program based on what you need to learn for data science and nothing else.
- Want more reasons,